[Note: This has been cross posted on the Adaptive Threat Division blog]
This is the first in the ‘Empire Series’, a set of articles that will cover various aspects of Empire’s functionality and usage. These posts will be split between various Empire authors and contributors with a running set of links updated at the top of each entry. While I’ve posted updates covering the different releases of Empire, we haven’t yet shown a huge amount of Empire’s operational usefulness (though @enigma0x3 did post an “Empire Tips and Tricks” article in August, as well as showing how Empire can be used with SCCM compromises). This post will focus on lateral spread with Empire- others will cover privilege escalation, persistence, data mining, situational awareness, TrollSploit, and more.
The “Empire Series”:
- 1/21/16 – Expanding Your Empire
- 1/28/16 – An Empire Case Study
Invoke-PsExec
PsExec has served us pentesters well for over a decade. Attackers love to use network administrators’ tools against them and PsExec is no exception. While we’re personally not the biggest fans of PsExec for lateral spread (and other teams have started to outgrow it just as we have) it is still a pentest staple and can be appropriate in specific situations.
Our custom implementation of PsExec (Invoke-PsExec) is based heavily on Metasploit’s approaches. It utilizes a reflection approach from exploit-monday.com in order to access underlying Window32 API functions, and operates as follows:
- OpenSCManagerA is used to open up a handle to the service control manager on a victim machine with SC_MANAGER_ALL_ACCESS (0xF003F) permissions.
- CreateServiceA is used with the resulting service control manage to create a new service with a specified name, set to launch a specified command.
- The service is then opened with OpenServiceA, started with StartServiceA, and execution pauses briefly for the service to start up and execute the given command.
- The service is then deleted with DeleteService.
This is obviously quite noisy (in that a service is created which a savvy defender could easily detect) but it has the advantage of giving us SYSTEM level execution on a target. All of this functionality is wrapped up in the lateral_movement/invoke_psexec module, which takes a Listener and ComputerName and handles all the configuration for you:

Invoke-WMI
Our preference for lateral spread is definitely WMI. While there are a few caveats with using WMI for lateral spread (see the kerberos ‘double hop’ problem), it’s significantly quieter than PsExec. Our implementation, lateral_movement/invoke_wmi, uses Invoke-WmiMethod -Path Win32_process -Name create … to trigger an Empire stager on a remote host to get execution. With the double hop problem, you need to remember that in most cases (unless a host allows unconstrained delegation) this new agent will not be able to access additional remote network resources. You will need to use runas/pth or steal a token in order to refresh the credentials for your currently running agent.

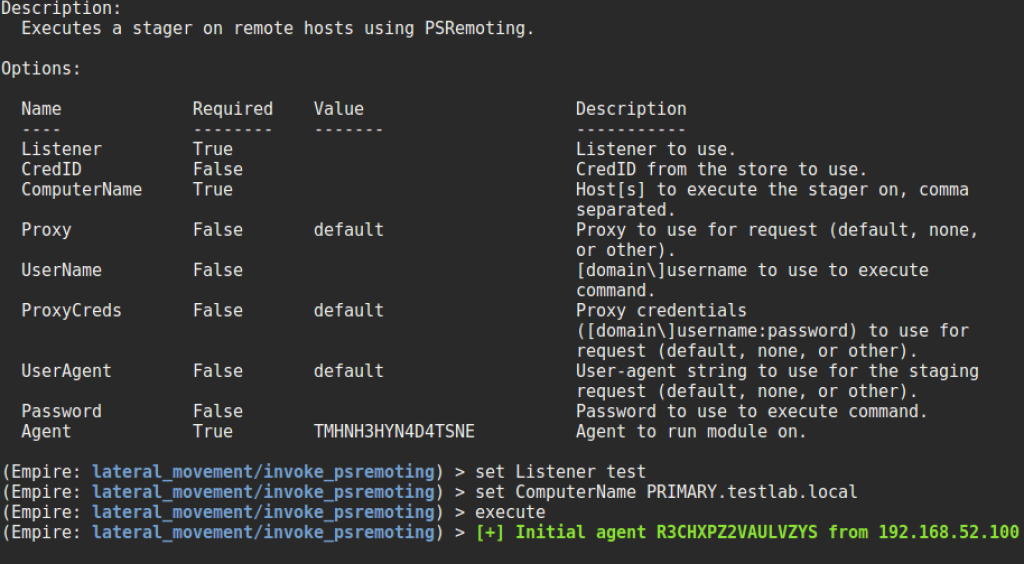
Invoke-PsRemoting
If Windows Remoting (WinRM) is enabled on a target, you can easily trigger an Empire agent remotely in the most “PowerShelly” way possible. By executing Invoke-Command on a remote system with the ScriptBlock set to Empire staging code, lateral spread is easy. Like Invoke-PsExec and Invoke-WMI, our implementation at lateral_movement/invoke_psremoting accepts a Listener and ComputerName. It also also accepts and optional UserName and Password (or a CredID specification) to run a stager with separate credentials on the remote host.
Invoke-WMIDebugger
One slightly novel lateral spread method we have is the ability to easily use WMI to set the debugger for any of the five Windows Accessibility binaries. These binaries include the notorious sethc.exe (‘Sticky Keys’, activated with shift x 5), Utilman.exe (the ‘Ease of Access’ button, activated with Win+U), Osk.exe (the on-screen keyboard, activated from the Utilman interface), Narrator.exe (text narration, also activated from the Utilman interface), and Magnify.exe (the screen maginifier, also activated from the Utilman interface). What’s great about these binaries is that they can be triggered from an RDP session BEFORE authentication! We use the registry ‘Image File Execution Options’ option instead of overwriting the binaries themselves, as this makes cleanup easier.
With lateral_movement/invoke_wmi_debugger you can set any of these binaries to trigger custom Empire staging code tied to your particular command and control server. If a listener is specified, the staging script is stored into the registry location specified by RegPath and launched by the specified binary. If a listener isn’t specified the program set in the Binary argument will launch instead (like cmd.exe):

There’s one caveat- if you trigger an agent using this method, you will need to keep the RDP window alive long enough to inject into another process. As soon as the RDP pre-auth session closes, your original agent will as well. You should have about 30 seconds of non-activity until your current RDP session closes.
When you’re done, specify the Cleanup argument and everything will be set back to normal. Of note: this method of backdooring usability binaries for lateral spread is something that some adversaries have done in the wild.
Passing the Hash
“But what about pass the hash??!” you may be yelling. We couldn’t have a complete toolset without SOME kind of option for hash passing, and again in the case Benjamin Delphy (the @gentilkiwi) comes to our rescue. Using Joseph Bialek‘s Invoke-Mimikatz implementation. we can execute Mimikatz’ sekurlsa::pth module. This allows us to spawn a new process and inject the specified NTLM hash into the process space, performing an ‘over-pass-the-hash‘ attack that effectively turns this credential into a Kerberos ticket. You can pass the hash either with the credentials/mimikatz/pth module or the shortcut from the Agent menu of pth <CredID> (utilizing the Empire credential store):

There are a few caveats with this approach. First, you need administrative privileges in order to execute it. And second, a new process will be spawned, so Empire’s implementation of Invoke-Mimikatz sets the new process to not spawn a new window. After the process executes, use steal_token (an alias for credentials/tokens, the integration of Joe’s Invoke-TokenManipulation script) in order to steal the token of the newly minted process.

Wrapup
Lateral spread is an important component of every penetration test and red team engagement. PsExec, WMI, “Debuggers”, WinRM, and PTH all have their place in engagements, and Empire aims to allow operators to choose the best method to fit their given situation.
